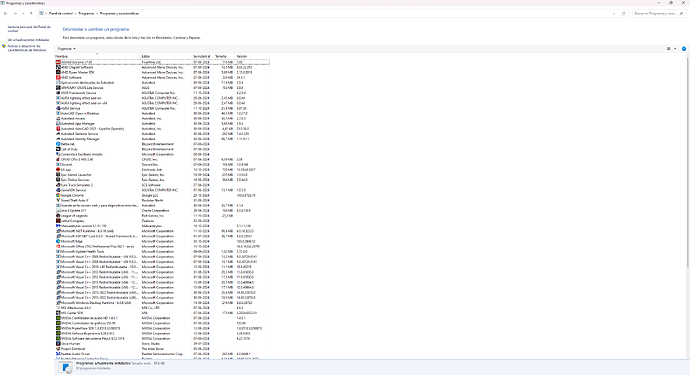
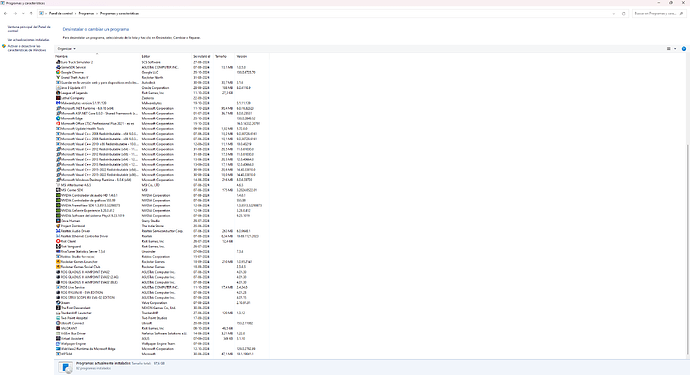
ahora el de mbar-log
Malwarebytes Anti-Rootkit BETA 1.10.3.1001
www.malwarebytes.org
Database version:
main: v2017.10.25.11
rootkit: v2017.10.14.01
Windows 10 x64 NTFS
Internet Explorer 11.1.22621.0
rococ :: DESKTOP-0IIUO9V [administrator]
18-10-2024 18:58:47
mbar-log-2024-10-18 (18-58-47).txt
Scan type: Quick scan
Scan options enabled: Anti-Rootkit | Drivers | MBR | Physical Sectors | Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken
Scan options disabled:
Objects scanned: 292283
Time elapsed: 3 minute(s), 17 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 2
C:\Windows\System32\atl.dll (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
C:\Windows\System32\atl.dll (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
Registry Keys Detected: 6
HKLM\SOFTWARE\CLASSES\CLSID\{44EC053A-400F-11D0-9DCD-00A0C90391D3} (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
HKLM\SOFTWARE\CLASSES\ATL.Registrar (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
HKLM\SOFTWARE\WOW6432NODE\CLASSES\ATL.Registrar (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
HKLM\SOFTWARE\CLASSES\WOW6432NODE\ATL.Registrar (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
HKLM\SOFTWARE\WOW6432NODE\CLASSES\CLSID\{44EC053A-400F-11D0-9DCD-00A0C90391D3} (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
HKLM\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{44EC053A-400F-11D0-9DCD-00A0C90391D3} (Trojan.FakeMS.ED) -> Delete on reboot. [456a7f600f9a043244f9fefc8878827e]
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
Physical Sectors Detected: 0
(No malicious items detected)
(end)
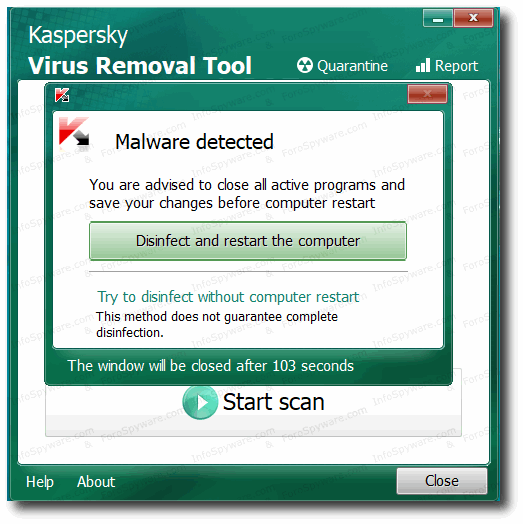
 para abrir el cuadro del ´´REPORTE´´ que genera para que me lo pueda enviar usted, tal y como se refleja en la siguiente pantalla:
para abrir el cuadro del ´´REPORTE´´ que genera para que me lo pueda enviar usted, tal y como se refleja en la siguiente pantalla: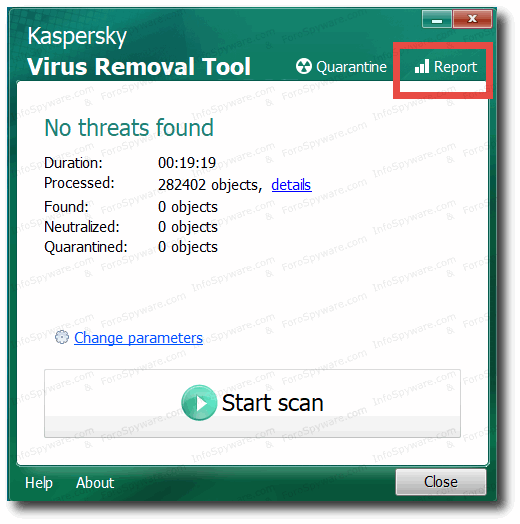
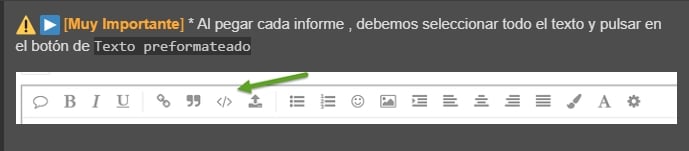
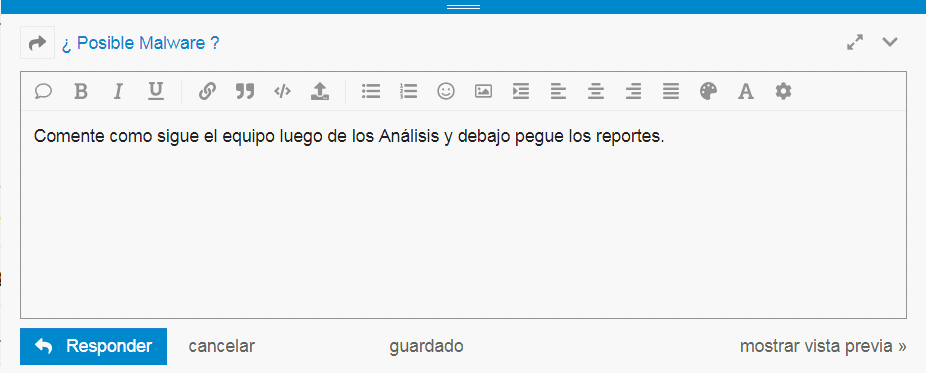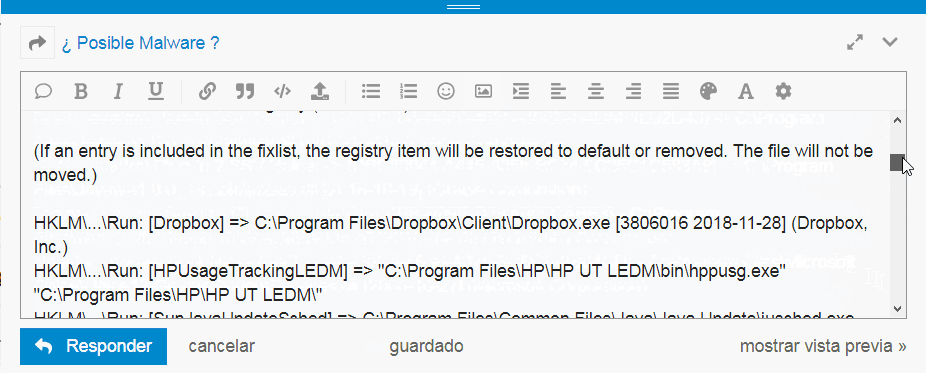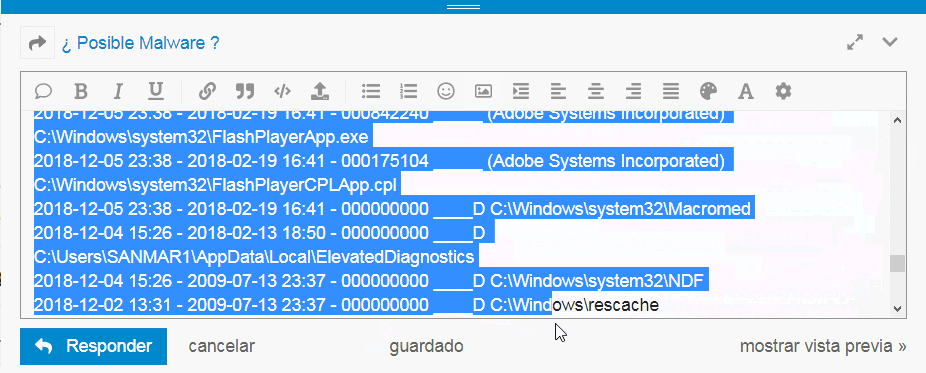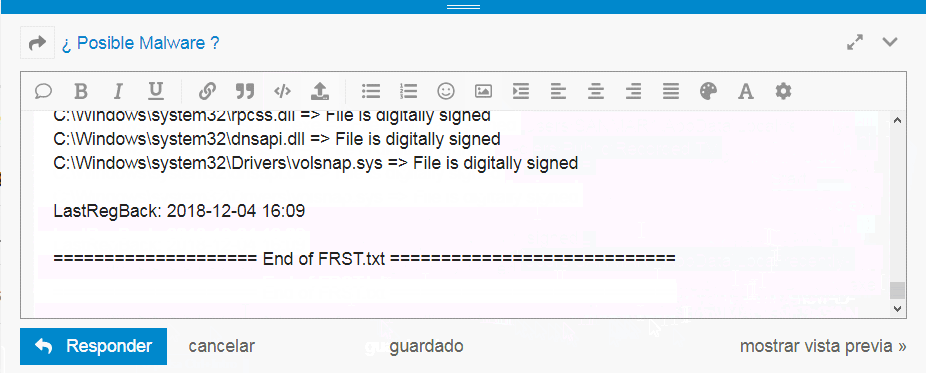
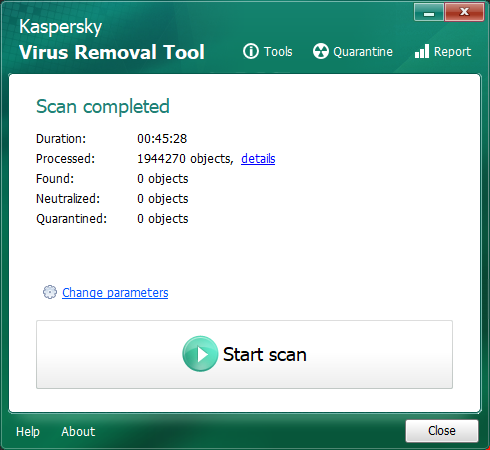
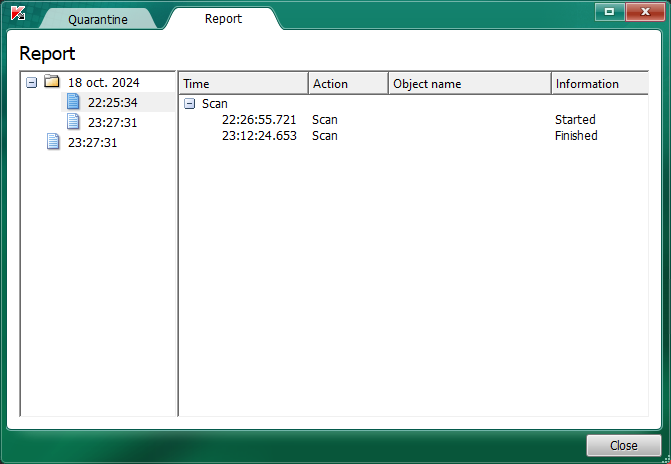
 tal y como aparece en la pantalla anterior.
tal y como aparece en la pantalla anterior.